“CompTIA CySA+” Exam CSO-001. Here you can get the latest free CSO-001 exam exercise questions and answers for free and easily improve your skills!
CSO-001 exam: The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to configure and use threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats and risks to an organization, with the end goal of securing and protecting applications and systems within an organization. Follow the link to find more information about https://www.leads4pass.com/cs0-001.html exam.
Watch the CompTIA CS0-001 video tutorial online
Table of Contents:
- Latest CompTIA CS0-001 pdf
- Test your CompTIA CS0-001 exam level
- Related CS0-001 Popular Exam resources
- Get Lead4Pass Coupons (12% OFF)
- What are the advantages of Lead4pass?
Latest CompTIA CS0-001 pdf
[PDF] Free CompTIA CS0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=1SWIrLCSj4qgOfB86uKdQYM0Tdc3XrRlK
Cloud+ (Plus) Certification | CompTIA IT Certifications:https://www.comptia.org/certifications/cloud
Free CompTIA CS0-001 Exam Practice Questions
QUESTION 1
Weeks before a proposed merger is scheduled for completion, a security analyst has noticed unusual traffic patterns on
a file server that contains financial information. Routine scans are not detecting the signature of any known exploits or
malware. The following entry is seen in the ftp server logs:
tftp –I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?
A. Continue to monitor the situation using tools to scan for known exploits.
B. Implement an ACL on the perimeter firewall to prevent data exfiltration.
C. Follow the incident response procedure associate with the loss of business critical data.
D. Determine if any credit card information is contained on the server containing the financials.
Correct Answer: C
QUESTION 2
A security analyst is reviewing the following log after enabling key-based authentication.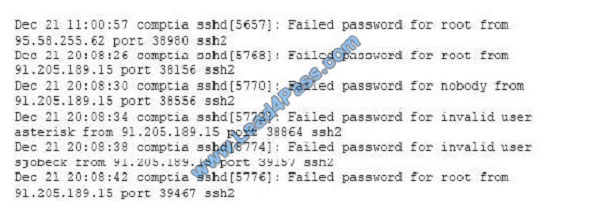
Given the above information, which of the following steps should be performed NEXT to secure the system?
A. Disable anonymous SSH logins.
B. Disable password authentication for SSH.
C. Disable SSHv1.
D. Disable remote root SSH logins.
Correct Answer: B
QUESTION 3
While a threat intelligence analyst was researching an indicator of compromise on a search engine, the web proxy
generated an alert regarding the same indicator. The threat intelligence analyst states that related sites were not visited
but were searched for in a search engine. Which of the following MOST likely happened in this situation?
A. The analyst is not using the standard approved browser.
B. The analyst accidently clicked a link related to the indicator.
C. The analyst has prefetch enabled on the browser in use.
D. The alert in unrelated to the analyst\\’s search.
Correct Answer: C
QUESTION 4
Which of the following is MOST effective for correlation analysis by log for threat management?
A. PCAP
B. SCAP
C. IPS
D. SIEM
Correct Answer: D
QUESTION 5
An analyst wants to use a command line tool to identify open ports and running services on a host along with the
application that is associated with those services and port. Which of the following should the analyst use?
A. Wireshark
B. Qualys
C. netstat
D. nmap
E. ping
Correct Answer: D
QUESTION 6
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL
vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and
the web server providing these services. After investigating the platform vulnerability, it was determined that the web
services provided are being impacted by this new threat.
Which of the following data types are MOST likely at risk of exposure based on this new threat? (Choose two.)
A. Cardholder data
B. Intellectual property
C. Personal health information
D. Employee records
E. Corporate financial data
Correct Answer: AC
QUESTION 7
A cybersecurity analyst has identified a new mission-essential function that utilizes a public cloud-based system. The
analyst needs to classify the information processed by the system with respect to CIA. Which of the following should
provide the CIA classification for the information?
A. The cloud provider
B. The data owner
C. The cybersecurity analyst
D. The system administrator
Correct Answer: B
QUESTION 8
A system administrator recently deployed and verified the installation of a critical patch issued by the company\\’s
primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely
execute code from over the network. However, the administrator just ran a vulnerability assessment of networked
systems, and each of them still reported having the same vulnerability. Which of the following is the MOST likely for
this?
A. The administrator entered the wrong IP range for the assessment.
B. The administrator did not wait long enough after applying the patch to run the assessment.
C. The patch did not remediate the vulnerability.
D. The vulnerability assessment returned false positives.
Correct Answer: C
QUESTION 9
A security analyst has noticed an alert from the SIEM. A workstation is repeatedly trying to connect to port 445 of a file
server on the production network. All of the attempts are made with invalid credentials. Which of the following describes
what is occurring?
A. Malware has infected the workstation and is beaconing out to the specific IP address of the file server.
B. The file server is attempting to transfer malware to the workstation via SMB.
C. An attacker has gained control of the workstation and is attempting to pivot to the file server by creating an SMB
session.
D. An attacker has gained control of the workstation and is port scanning the network.
Correct Answer: C
QUESTION 10
An employee at an insurance company is processing claims that include patient addresses, clinic visits, diagnosis
information, and prescription. While forwarding documentation to the supervisor, the employee accidentally sends the
data to a personal email address outside of the company due to a typo. Which of the following types of data has been
compromised?
A. PCI
B. Proprietary information
C. Intellectual property
D. PHI
Correct Answer: D
QUESTION 11
A technician is running an intensive vulnerability scan to detect which ports are open to exploit. During the scan, several
network services are disabled and production is affected. Which of the following sources would be used to evaluate
which network service was interrupted?
A. Syslog
B. Network mapping
C. Firewall logs
D. NIDS
Correct Answer: A
QUESTION 12
A company has received the results of an external vulnerability scan from its approved scanning vendor. The company
is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement of the scan results. Which
of the following contract breaches would result if this remediation is not provided for clients within the time frame?
A. Service level agreement
B. Regulatory compliance
C. Memorandum of understanding
D. Organizational governance
Correct Answer: A
QUESTION 13
A cyber incident response team finds a vulnerability on a company website that allowed an attacker to inject malicious
code into its web application. There have been numerous unsuspecting users visiting the infected page, and the
malicious code executed on the victim\\’s browser has led to stolen cookies, hijacked sessions, malware execution, and
bypassed access control. Which of the following exploits is the attacker conducting on the company\\’s website?
A. Logic bomb
B. Rootkit
C. Privilege escalation
D. Cross-site scripting
Correct Answer: D
Related CS0-001 Popular Exam resources
| title | youtube | CompTIA | lead4pass | Lead4Pass Total Questions | |
|---|---|---|---|---|---|
| CompTIA | lead4pass CS0-001 dumps pdf | lead4pass CS0-001 youtube | CompTIA (CySA+) Cybersecurity Analyst+ Certification | https://www.leads4pass.com/cs0-001.html | 402 Q&A |
Get Lead4Pass Coupons(12% OFF)
What are the advantages of Lead4pass?
Lead4pass employs the most authoritative exam specialists from CompTIA, Cisco, Microsoft, IBM, Oracle, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose Lead4Pass to pass the exam with ease!
Summarize:
It’s not easy to pass the CompTIA exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. Lead4pass provides you with the most relevant learning materials that you can use to help you prepare.
