Use the latest 200-201 dumps to help you pass the Cisco CBROPS certification exam

Using 200-201 dumps can help you successfully pass the Cisco CBROPS certification exam on your first attempt.
Because 200-201 dumps have many success advantages:
- Lightweight Learning Tool (PDF+VCE)
- More free usage time (365 days Free Update)
- Covers all Cisco CBROPS practical exam questions and answers, with explanations of difficult problems
- Have a professional Cisco technical team service
So why not use 200-201 dumps to help you easily and successfully pass the exam? And leads4pass, as the provider of 200-201 dumps, has many years of industry reputation, is the industry leader, and is trustworthy, what else do you have to worry about?
Therefore, it is strongly recommended that you use the 200-201 dumps exam material https://www.leads4pass.com/200-201.html, which is up to date throughout the year, to prepare you for a career leap.
More detailed 200-201 CBROPS certification information:
Vendor: Cisco
Exam Code: 200-201
Exam Name: Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS)
Certification: CyberOps Associate
Duration: 120 minutes
Languages: English
Price: $300 USD
Number of Questions: 95-105
200-201 dumps: https://www.leads4pass.com/200-201.html (Total Questions: 245 Q&A)
Cisco 200-201 exam questions online practice test:
Tips: Verify the answer at the end of the article
Question 1:
Refer to the exhibit.
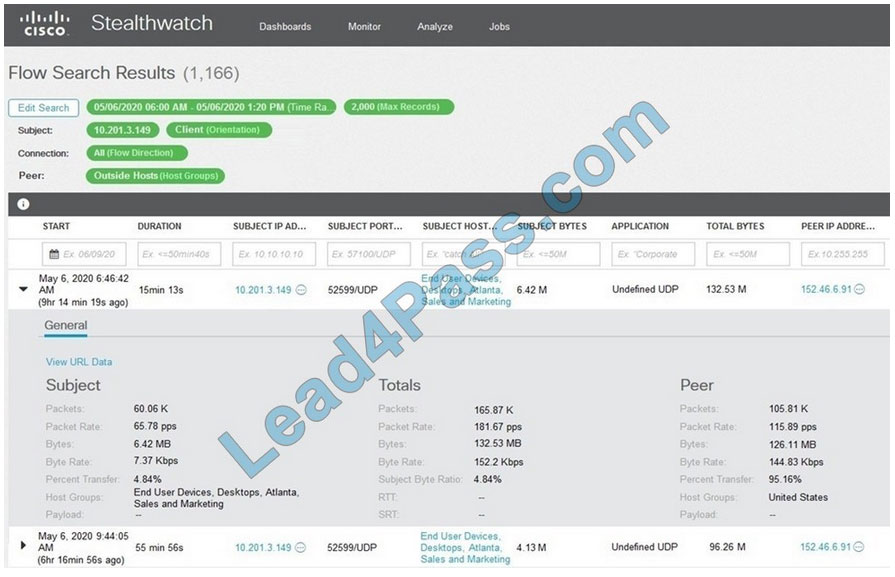
What is the potential threat identified in this Stealthwatch dashboard?
A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Question 2:
What does cyber attribution identify in an investigation?
A. cause of an attack
B. exploit of an attack
C. vulnerabilities exploited
D. threat actors of an attack
Question 3:
Refer to the exhibit.
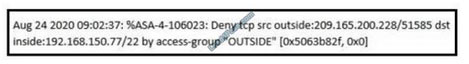
An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
A. indirect
B. circumstantial
C. corroborative
D. best
Question 4:
What is a sandbox interprocess communication service?
A. A collection of rules within the sandbox that prevent communication between sandboxes.
B. A collection of network services that are activated on an interface, allowing for inter-port communication.
C. A collection of interfaces that allow for coordination of activities among processes.
D. A collection of host services that allow for communication between sandboxes.
Question 5:
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
A. reconnaissance
B. action on objectives
C. installation
D. exploitation
Question 6:
What is the practice of giving an employee access to only the resources needed to accomplish their job?
A. principle of least privilege
B. organizational separation
C. separation of duties
D. need to know principle
Question 7:
Refer to the exhibit
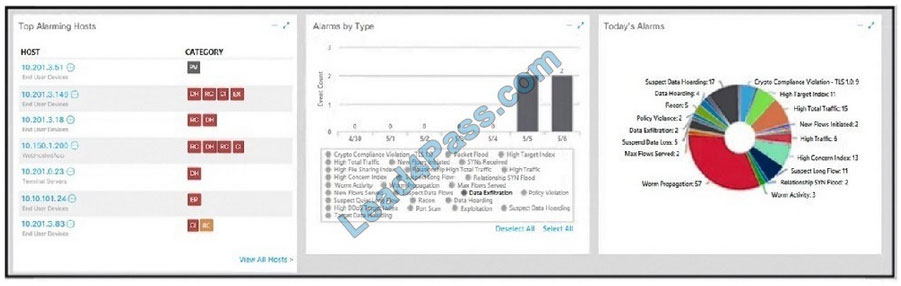
What is the potential threat identified in this Stealthwatch dashboard?
A. A policy violation is active for host 10.10.101.24.
B. A host on the network is sending a DDoS attack to another inside host.
C. There are two active data exfiltration alerts.
D. A policy violation is active for host 10.201.3.149.
Question 8:
Which incidence response step includes identifying all hosts affected by an attack?
A. detection and analysis
B. post-incident activity
C. preparation
D. containment, eradication, and recovery
Question 9:
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
A. availability
B. confidentiality
C. scope
D. integrity
Question 10:
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A. MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
B. MAC is the strictest of all levels of control and DAC is object-based access
C. DAC is controlled by the operating system and MAC is controlled by an administrator
D. DAC is the strictest of all levels of control and MAC is object-based access
Question 11:
What is vulnerability management?
A. A security practice focused on clarifying and narrowing intrusion points.
B. A security practice of performing actions rather than acknowledging the threats.
C. A process to identify and remediate existing weaknesses.
D. A process to recover from service interruptions and restore business-critical applications
Question 12:
Which type of evidence supports a theory or an assumption that results from initial evidence?
A. probabilistic
B. indirect
C. best
D. corroborative
Question 13:
What is the difference between deep packet inspection and stateful inspection?
A. Deep packet inspection gives insights up to Layer 7, and stateful inspection gives insights only up to Layer 4.
B. Deep packet inspection is more secure due to its complex signatures, and stateful inspection requires less human intervention.
C. Stateful inspection is more secure due to its complex signatures, and deep packet inspection requires less human intervention.
D. Stateful inspection verifies data at the transport layer and deep packet inspection verifies data at the application layer
Question 14:
A company encountered a breach on its web servers using IIS 7 5 During the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
A. Upgrade to TLS v1 3.
B. Install the latest IIS version.
C. Downgrade to TLS 1.1.
D. Deploy an intrusion detection system
Question 15:
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
A. examination
B. investigation
C. collection
D. reporting
……
Verify answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | D | D | C | C | C | A | C | D | D | B | C | D | B | B | C |
The CyberOps Associate certification exam covers knowledge and skills related to security concepts, security monitoring, host-based analysis, network intrusion analysis, and security policies and procedures. The Core exam (200-201 CBROPS) is unique.
Select leads4pass 200-201 dumps https://www.leads4pass.com/200-201.html, Helping you 100% pass the Cisco 200-201 CBROPS certification exam.
